New! Free Assisted Migration to Anaconda’s Data Science Platform

Chandler Vaughn
Open-source software (OSS) is at the heart of innovative technologies and some of the most impressive AI successes being implemented today. It’s also the target of threat actors who seek to leverage the inherent risk of open source. The White House and the National Institute of Standards and Technologies (NIST) have issued guidance for organizations using Python and OSS, and now is the time to prepare for security challenges, especially if your organization is operating in the United States.
This article is a primer on these challenges, with recommendations for organizations.
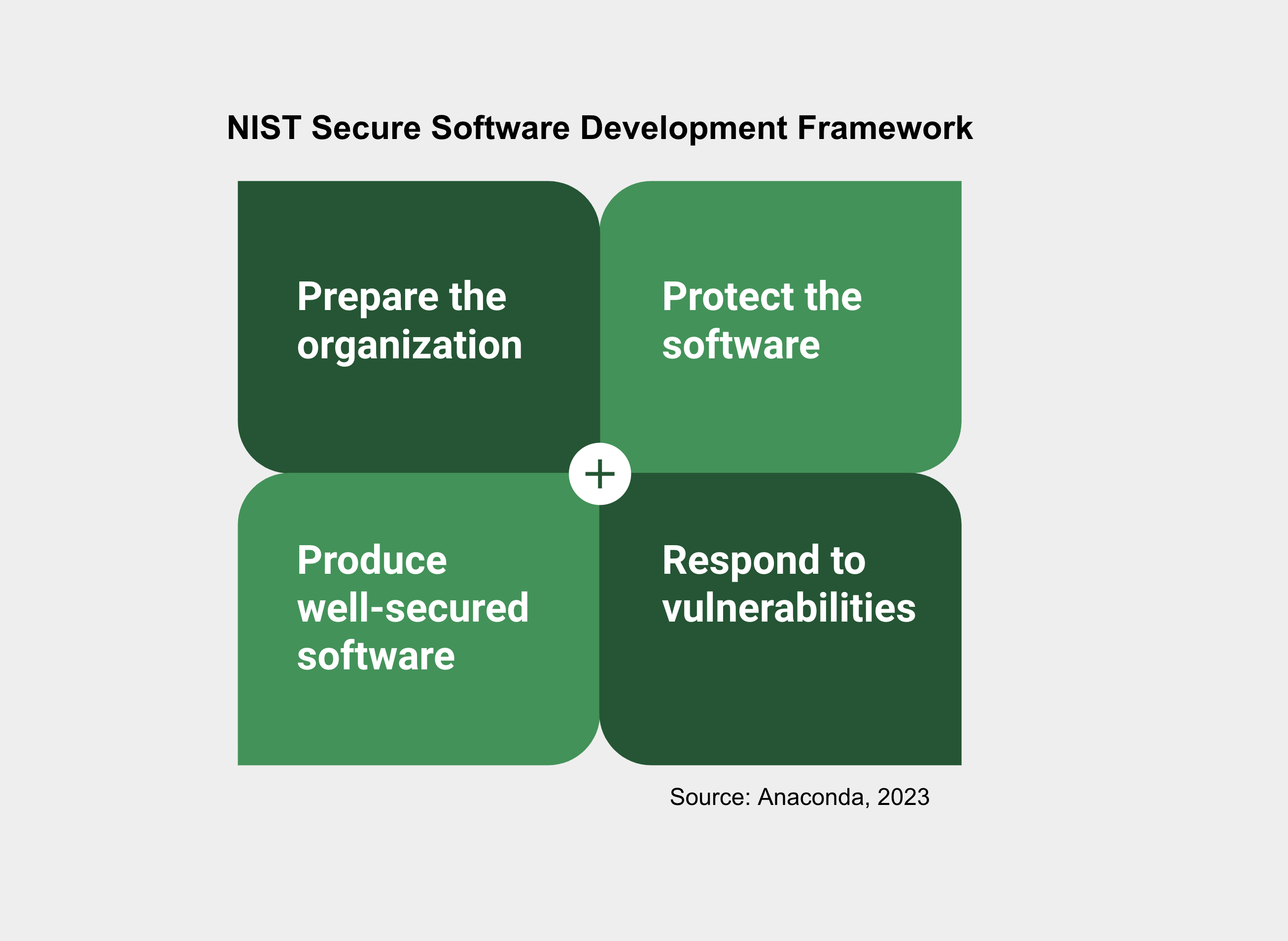
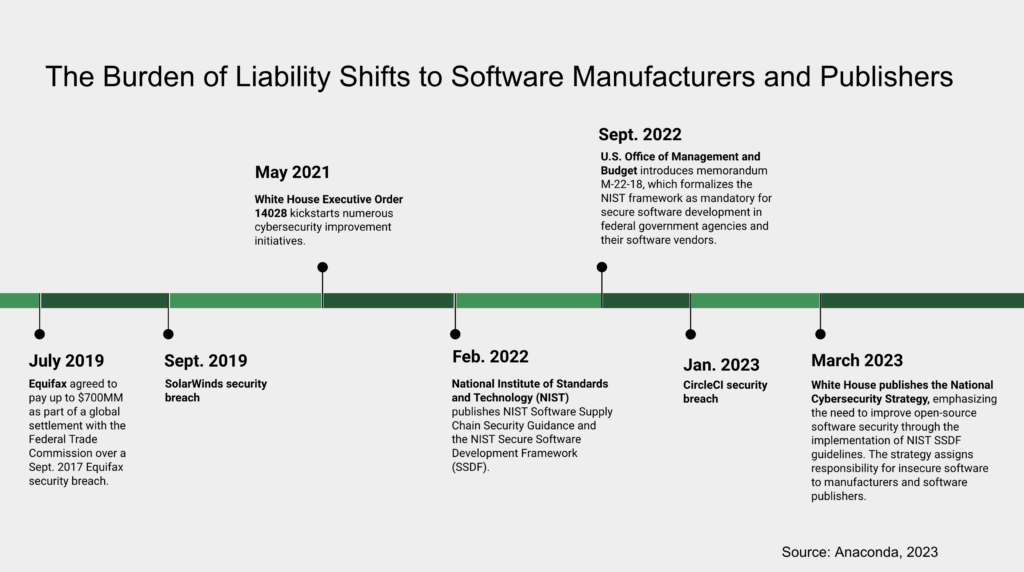
In May 2021, the White House issued Executive Order 14028, which kickstarted numerous cybersecurity improvement initiatives. In February 2022, as directed by this Executive Order, the National Institute of Standards and Technology (NIST) published NIST Software Supply Chain Security Guidance and the NIST Secure Software Development Framework (SSDF). The framework is comprised of four main categories:
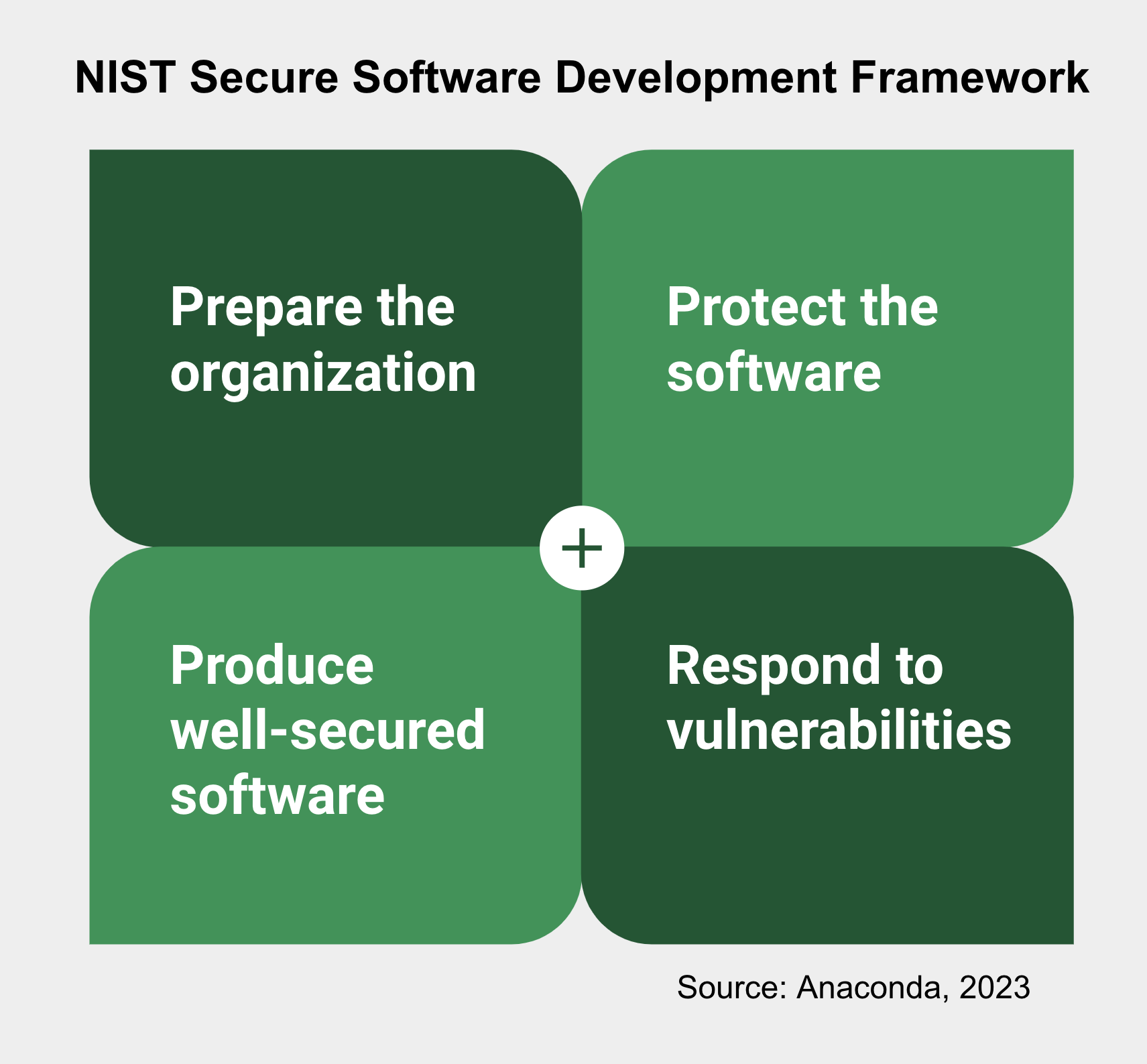
Traditionally, organizations have taken reactive measures for software security. However, the NIST SSDF emphasizes the need for proactive efforts, especially when it comes to open-source software. The complexity of open source, including dependency relationships and varying security practices, poses challenges.
In September 2022, the U.S. Office of Management and Budget introduced memorandum M-22-18, which formalized the NIST framework as mandatory for secure software development in federal government agencies and their software vendors. According to M-22-18, organizations selling software to the U.S. government must self-attest compliance with the NIST guidelines by June 2023 for critical software and September 2023 for all other software.
In March 2023, the White House published the National Cybersecurity Strategy, emphasizing the need for a collective defense and improving the security of the digital ecosystem, which includes open-source software. The strategy, which highlights the importance of adopting the NIST Cybersecurity Framework across sectors to improve cybersecurity practices and resilience, assigns responsibility for insecure software to manufacturers and software publishers rather than consumers or open-source developers:
“We must begin to shift liability onto those entities that fail to take reasonable precautions to secure their software while recognizing that even the most advanced software security programs cannot prevent all vulnerabilities.”
-National Cybersecurity Strategy
The specific legislative details regarding the implementation of the National Cybersecurity Strategy by the administration and Congress are still evolving. However, it is important for all software teams, especially those handling sensitive consumer or business data in sectors like financial services or healthcare, to be mindful of previous cases such as the $700-million fine imposed on Equifax by the Federal Trade Commission due to a vulnerability in the Apache Struts open-source project, resulting in the exposure of millions of sensitive consumer records.
Open-source software offers numerous benefits, including flexibility, cost-effectiveness, and rapid innovation. However, it also carries inherent vulnerabilities. Organizations that work with sensitive data or in highly regulated industries may expose themselves to potential risks when using platforms like PyPI or conda-forge, and these responsible open-source software maintainers have cautioned makers that these packages are not for business use.
These platforms host various packages from myriad sources. While many open-source communities have processes in place to review and vet code, not all packages undergo the same level of rigorous security checks. This could lead to the inadvertent introduction of insecure or malicious code into your systems in the form of typosquatting, malware, dependency confusion, and/or author impersonation. Additionally, the open nature of these platforms makes them attractive targets for threat actors who may attempt to compromise popular packages or distribute malicious ones.
Recommendation:
Review all vendors in your open-source software supply chain, and note all vendors who provide you with software or services related to security. Look for opportunities to centralize package and environment management with one platform, which will help ensure your organization’s open-source software users are selecting packages from a central location that meets your organization’s security requirements.
Scanning for common vulnerabilities and exposures (CVEs) is important. But you must go further than that—with CVE curation by experts—to ensure secure open-source packages and environments. You’ll also want tokenized access to software packages, centralized and managed by your IT administrators, for more robust security.
Policy controls and enforcement are not just an option—they are a necessity. In an era where data breaches are increasingly common and costly, robust security policies and controls are your first line of defense against cyber threats. They help prevent unauthorized access, detect anomalies, and respond to incidents.
However, the open-source nature of platforms like PyPI or conda-forge can make implementing and maintaining these measures complex and resource intensive. This often involves assembling multiple bespoke solutions to scan, control artifacts, and build policies.
Recommendation:
Evaluate your organization’s OSS supply chain governance and compliance, and check with vendors to see if they have a policy engine to assist your security efforts across the organization. Further, see if they can help you set up custom policies for different teams so you can limit access to deployment or production environments to only those who require it.
Navigating the complexities of compliance with government regulations is a daunting task. The 2023 National Cybersecurity Strategy and Executive Order 14028 emphasize the shared responsibility of all stakeholders in securing the digital ecosystem. These regulations lay out specific requirements for organizations, including conducting risk assessments, implementing security measures, and reporting incidents. Non-compliance can lead to penalties and reputational damage.
Achieving and maintaining compliance in the face of these complex regulations and the ever-evolving cybersecurity landscape can be overwhelming. This is where having a trusted partner becomes invaluable.
Recommendation:
Choose your open-source vendors carefully. Consult buyer’s guides, third-party and user reviews, and other resources to determine if the promises vendors make are evident in their solutions. Consider vendors’ years of experience, the quality of their teams, and their support options in addition to their products. You will want all partners to be as committed to security as your organization, as your team will bear the liability responsibility.
It is important for you to take proactive steps to secure software across your organization. Anaconda’s solutions align with these national strategies and the fundamental principles of the NIST framework by providing tools and features that help enforce crucial policies and controls, ensuring your open-source software ecosystem is secure and compliant right from the start. While we recognize that no system can be completely impervious to threats, our products are meticulously designed to provide unparalleled security, safeguarding your data and systems in an increasingly interconnected digital landscape.
With Anaconda, we’ve done the hard work for you. When you download from Anaconda, you’re downloading something we’ve built and secured from the ground up. We provide tools and features that help enforce crucial policies and controls, ensuring your open-source software ecosystem is secure and compliant from the beginning. We created our platform so you can focus on what you do best, knowing your open-source supply chain is in safe hands.
Here’s how Anaconda can help you navigate the evolving landscape of cybersecurity responsibilities:
When you choose Anaconda, you get the capabilities to build secure Python solutions faster—and you’re investing in the future of your organization’s security. With Anaconda in place as your enterprise platform, you are demonstrating your commitment to taking reasonable precautions to secure your software.
To learn more about how Anaconda can help you build secure Python solutions faster, book a free security consultation or schedule a demo today.
Talk to one of our experts to find solutions for your AI journey.