Anaconda is pleased to announce the release of conda signature verification. This feature preserves conda install integrity by verifying package artifacts and metadata against a chain of trust.
Benefits of conda signature verification
When conda verifies artifact signatures, it assures users that packages they are about to install are exactly as they were when produced on our secure build network. This verification step eliminates many potential single points of failure in the software supply chain — substantially reducing the impact on customer systems from possible man-in-the-middle attacks, compromised mirrors, or content distribution networks, TLS misconfiguration, and more. This greatly secures our package distribution system from being an attack vector for client systems, and arms users with information about possible compromises.
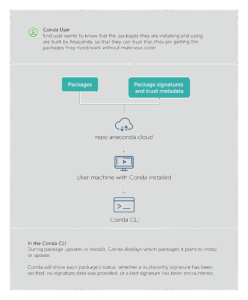
Conda signature verification ensures that when users obtain a package, or data about that package, they can know whether it is trustworthy and that the package comes from a reliable source and has not been tampered with.
How do we sign and verify artifacts?
The conda signature verification design is based on The Update Framework (TUF). Originally developed in 2009, TUF was designed as a solution to address the widespread vulnerabilities of package managers. TUF provides a flexible framework and specification that developers can adopt into any software update system to defend against a wide range of attacks, even against sophisticated attackers that compromise the repository or verification keys.
After Anaconda has built a package, the package and its metadata are signed, producing a signature on our secure build network. The package and corresponding signature metadata are then uploaded to Anaconda’s premium repository.
When conda obtains these packages, conda verifies that the signatures come from trusted signers and match the package data. Trust is established using root metadata — which ships with conda — to delegate to verification authorities. In short, root metadata vouches for package signers. And root metadata is also kept securely updated with root chaining: conda uses the version it currently trusts to verify the next version of root metadata. Anaconda has carefully controlled, secure procedures for root key management, requiring a consensus of multiple authorities in separate locations using offline keys, each created and kept only on hardware security devices.
By carefully separating security responsibilities into a root trust authority, a key manager authority, and package verification authorities, we achieve a compromise-resilient, flexible and extendable, and robust security solution. As a result, even if an attacker has compromised a repository server or mirror, conda can still tell if a package or its metadata has been tampered with after we’ve built them, and users can still reject modified packages. Further, even if there is a compromise of the verification process itself on our own secure build network, conda can determine whom to trust by using root metadata.
Who will have access to conda signature verification, and how?
Initially, users of our professional repository (repo.anaconda.cloud) will need to make a few updates to turn this feature on. Please refer to the install instructions and expected results here to get started.