There are currently three primary methods for integrating packages into a channel on Package Security Manager (PSM) on prem:
- Creating mirrors
- Copying/moving packages from another channel
- Manual uploads
However, these current methods have some limitations regarding security filtering and their ability to be replicated across multiple channels.
How Package Management Works Now
Most PSM users rely on mirroring to bring packages into their repositories and keep their repositories updated by scheduling mirror updates on a daily, weekly, or monthly basis. A Common Vulnerabilities and Exposure (CVE) mirror, on the other hand, runs every four hours, ensuring timely updates on vulnerabilities.
Despite this, a critical gap remains: if a new CVE is identified, vulnerable packages can still exist in the repository until the next scheduled mirror runs. This creates a window of opportunity for serious security risks, as users may inadvertently install these vulnerable packages.
Administrative users can manually move vulnerable packages to a restricted channel or delete them before the next mirror cycle but this can be time consuming.
Introducing Policy Filters
Users will now have the ability to create policy filters, which will allow for more robust security measures.
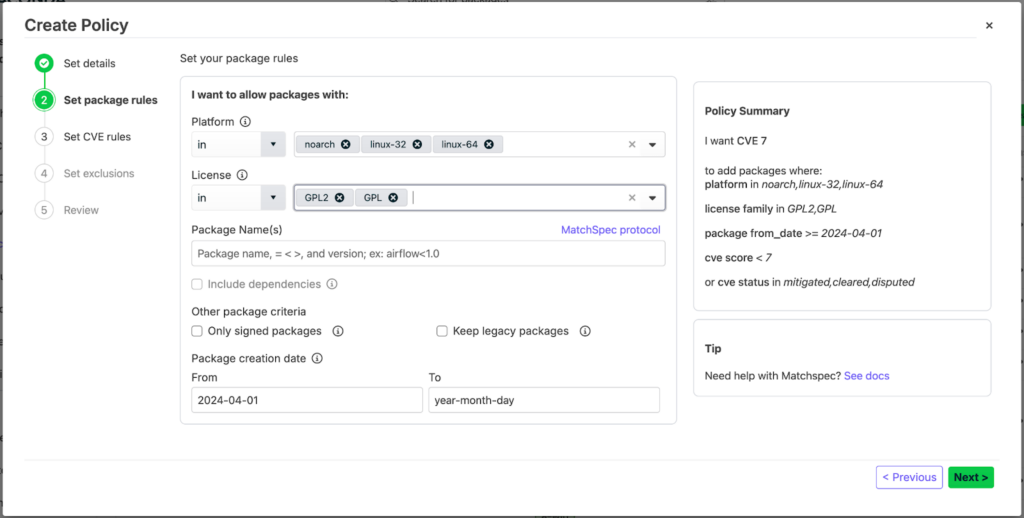
Here is how it will work: Policies will be applied at the channel level, enabling administrators to set specific rules—such as allowing only packages with a CVE score below 7. This can be applied across multiple channels, streamlining the management process.
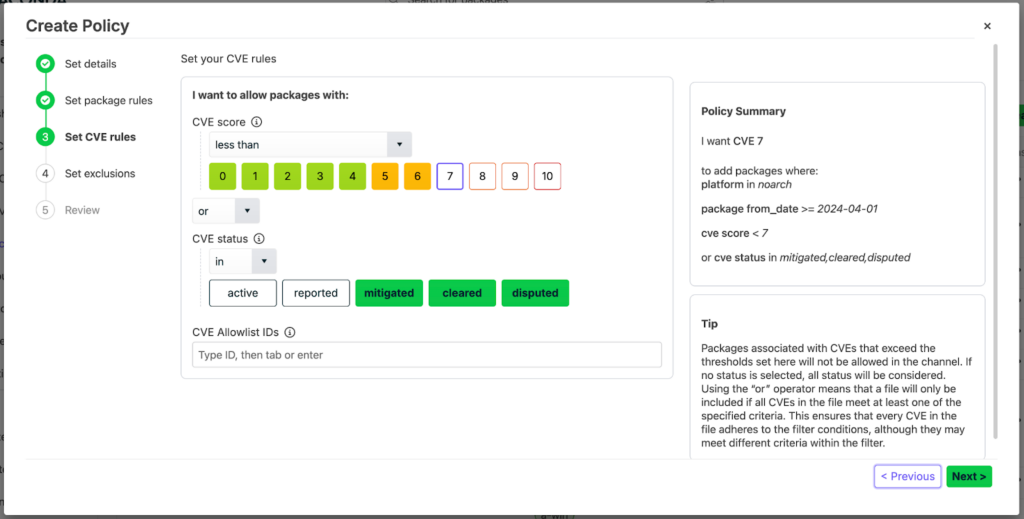
Users of Anaconda’s Package Security Manager will automatically have access to this new policy capability once they upgrade their organization’s PSM to version 6.7.0. Otherwise, this new feature will not be available.