Understanding CVEs
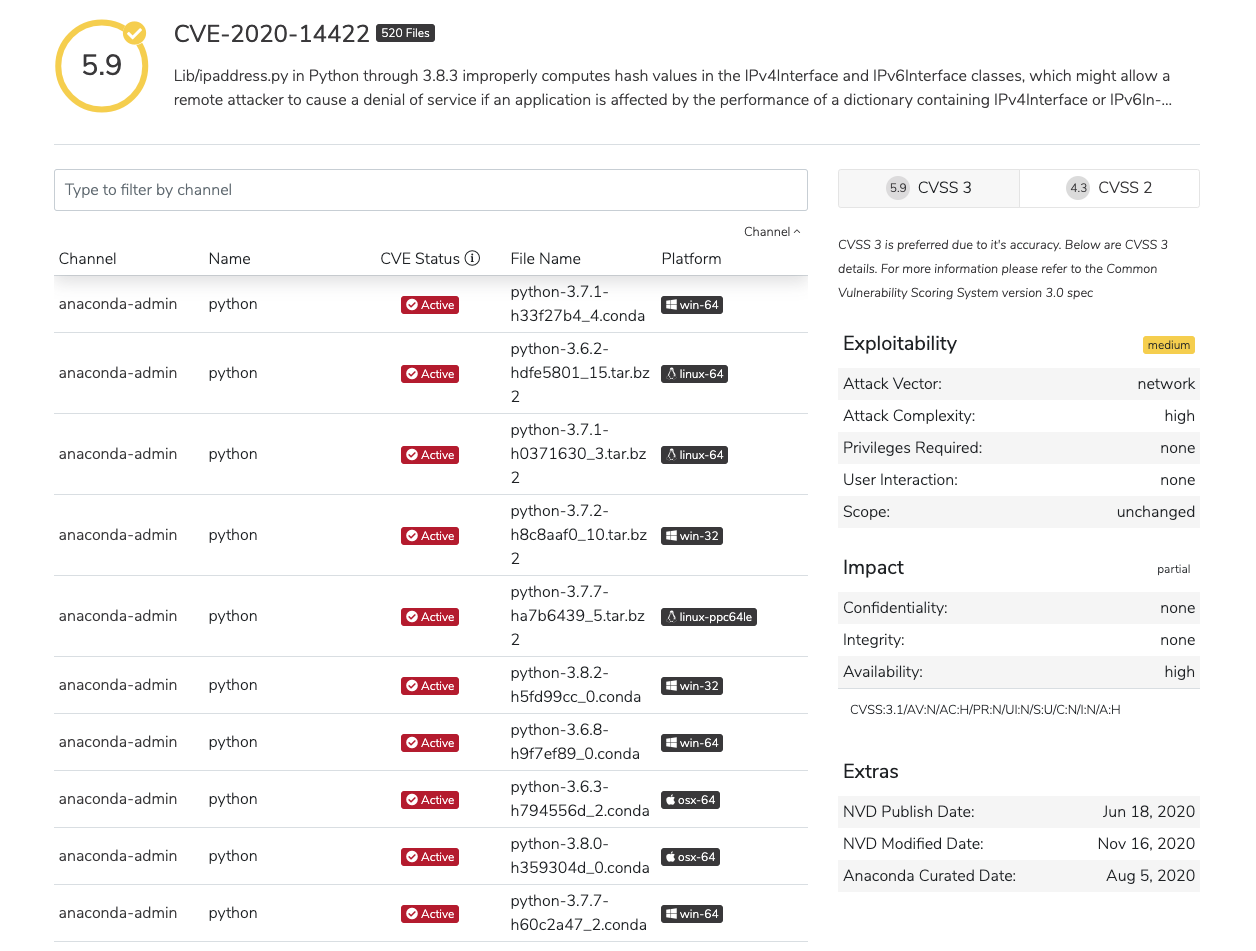
CVE scores
Severity scores are assigned based on the numerical Common Vulnerability Scoring System (CVSS) on a zero to ten scale.| CVSS score | Qualitative Rating |
|---|---|
| 0 | None |
| 0.1 - 3.9 | Low |
| 4.0 - 6.9 | Medium |
| 7.0 - 8.9 | High |
| 9.0 - 10 | Critical |
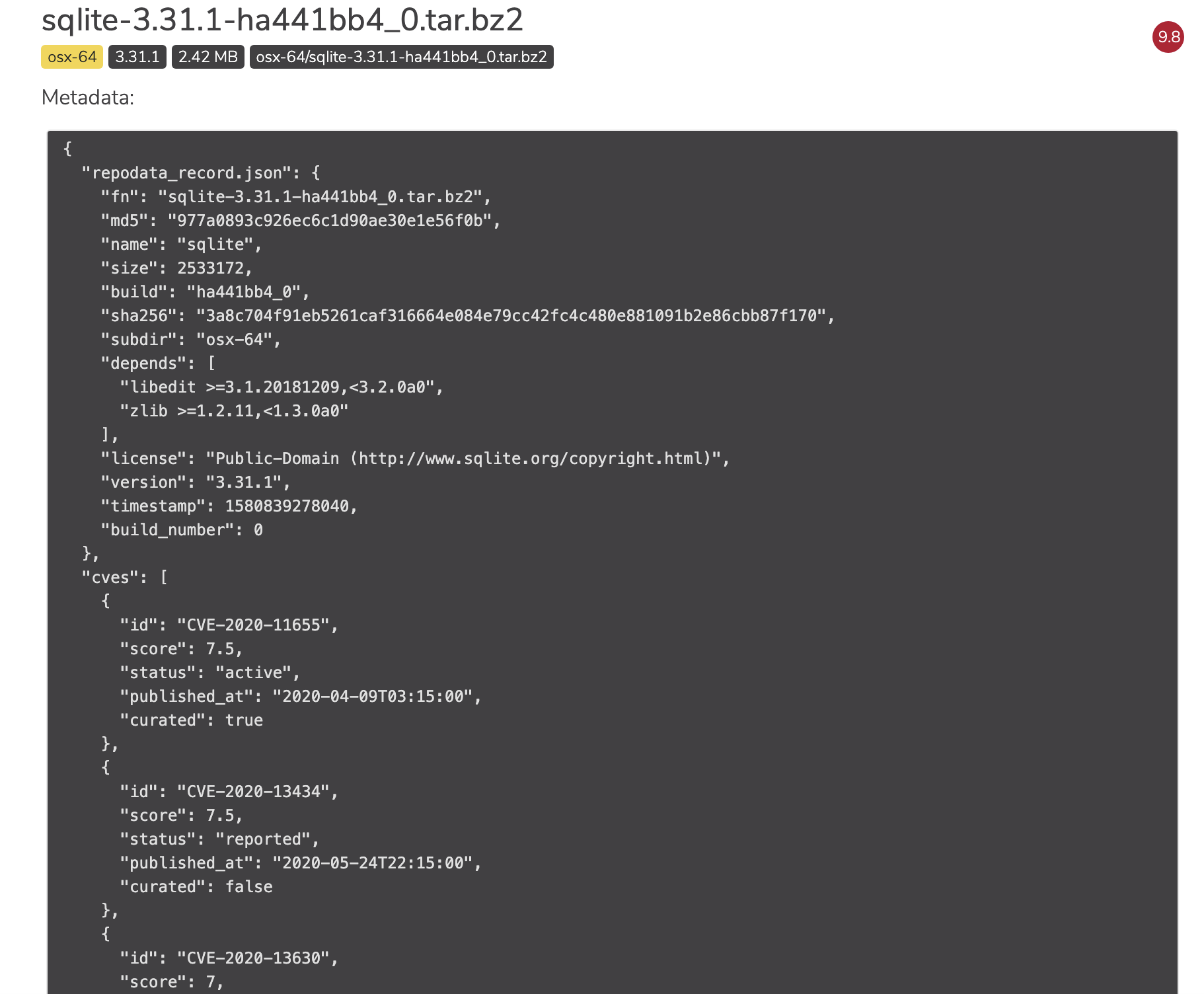
CVE curation
The CVE curation process can be summarized in four steps:- Anaconda sources Team Edition’s CVE information from the National Institute of Standards and Technology(NIST) National Vulnerability Database (NVD).
- From there, NVD CVE information is matched with the package names and versions in the Anaconda repository.
- Each auto-matched CVE is examined for accuracy by Anaconda staff. The CVEs get one or more reviews to categorize, refine, and improve the reported information.
- The refined CVE metadata allows you to learn more about each vulnerability and filter out OSS packages that don’t meet your security requirements.
CVE statuses
CVE descriptions include one of five CVE status categories. “Reported” is a CVE from NIST that has not been reviewed by the Anaconda Team. All other categories have been curated and their labels feature a check mark: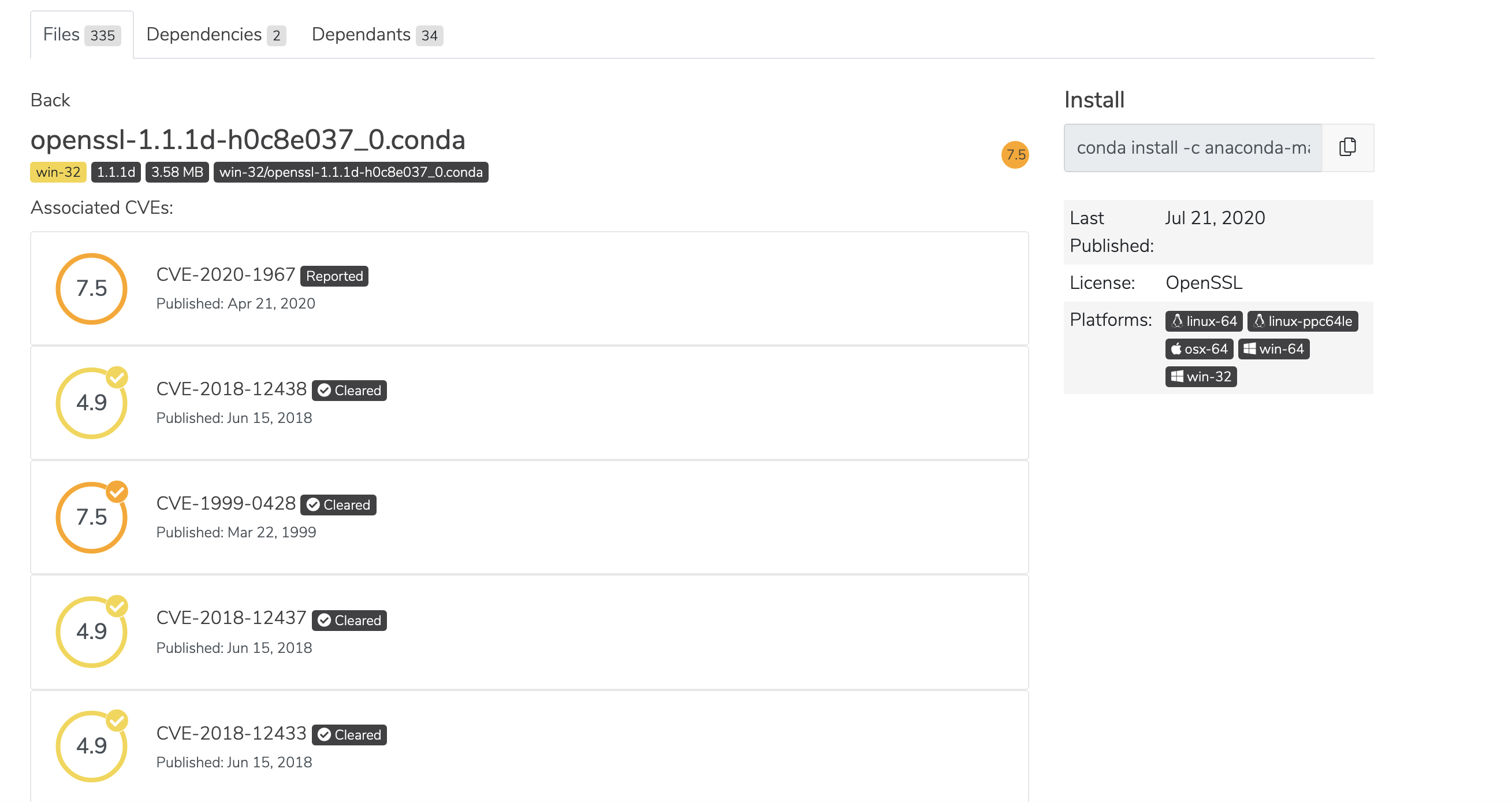
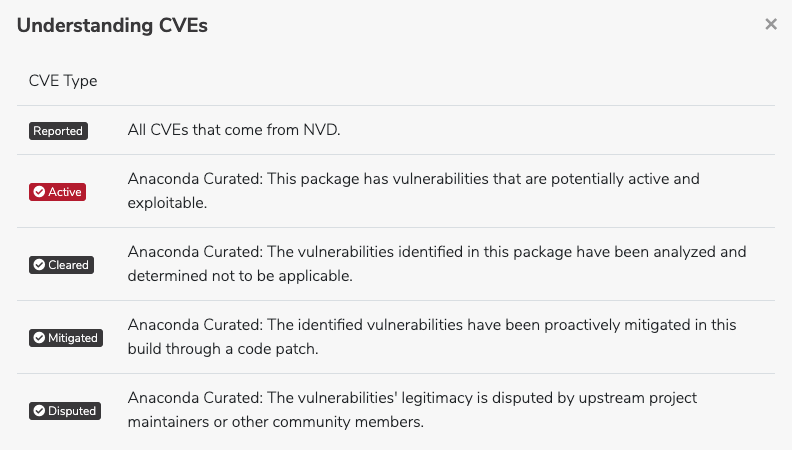
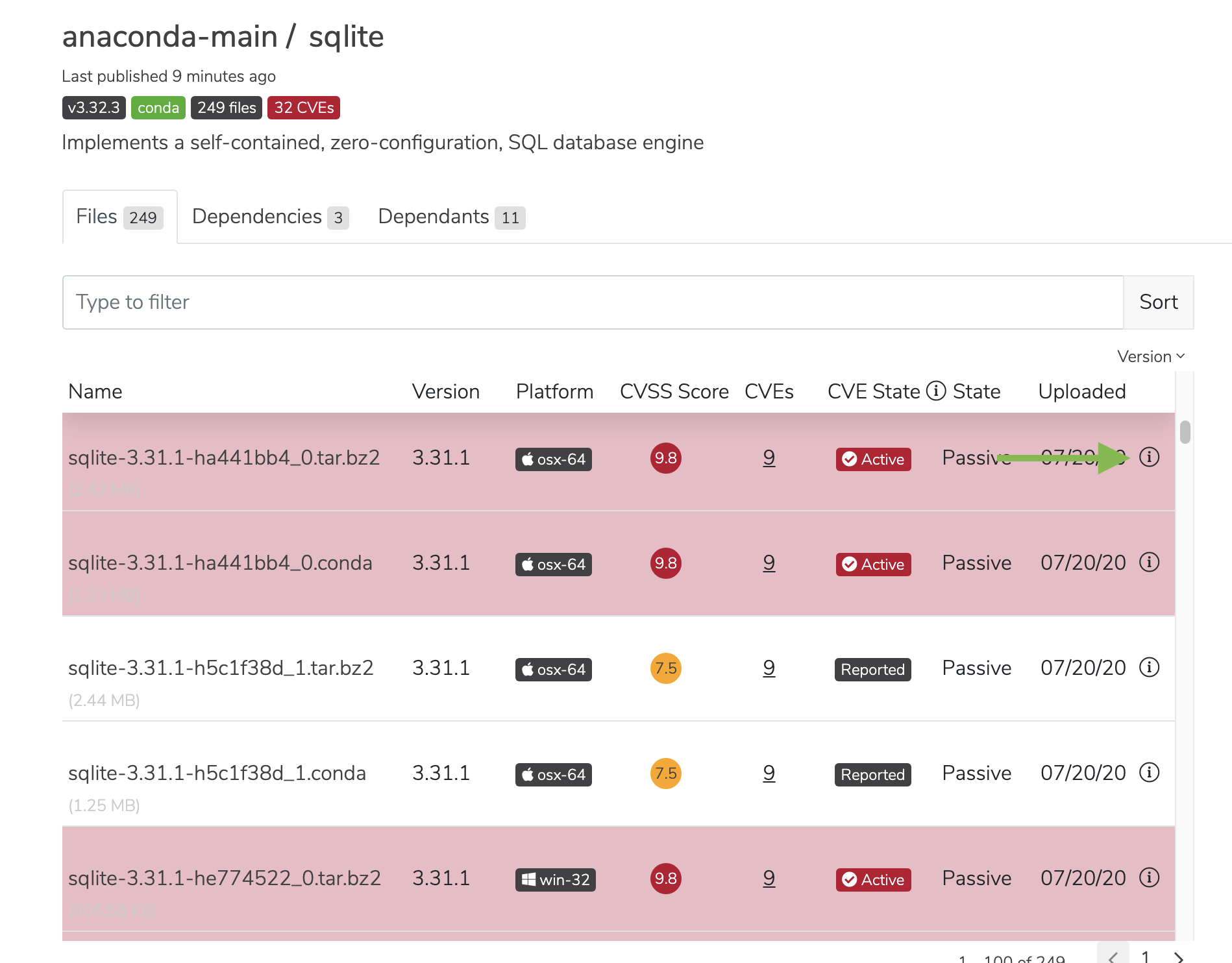
CVE labels and tabs
The number located on the CVE tab only indicates the number of CVEs pertaining to the packages within that channel: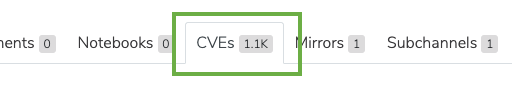
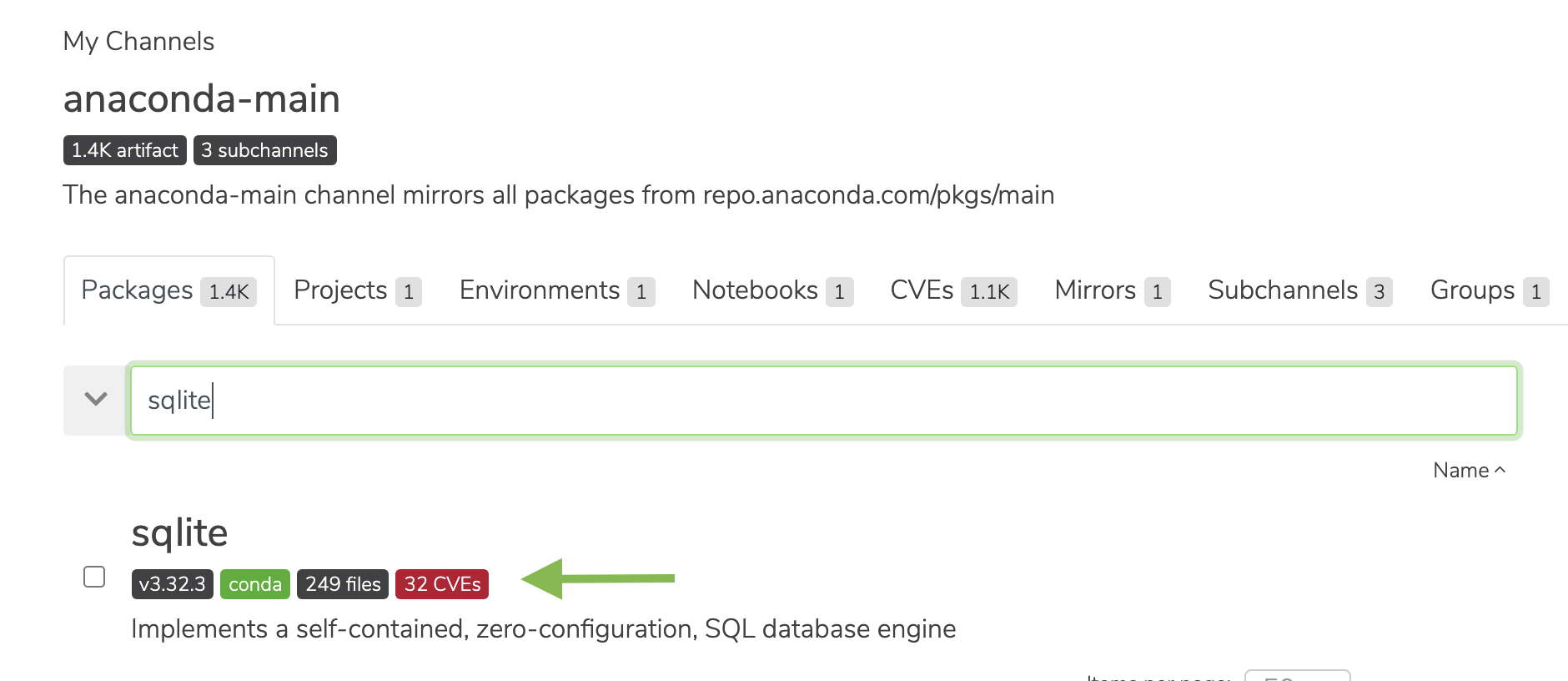
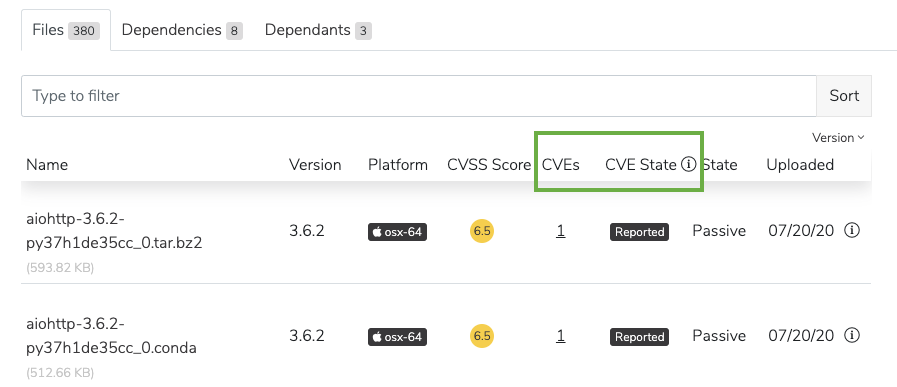
Listing the latest CVEs
As an administrator, you are able to view the latest published CVEs. Via the UI You can view a list of the latest CVEs at the top of the dashboard. Additionally, you can click Show more at the bottom of the list to view a larger list of CVEs. CVEs are sorted by their Anaconda Curated date, followed by published CVEs that have yet to be curated.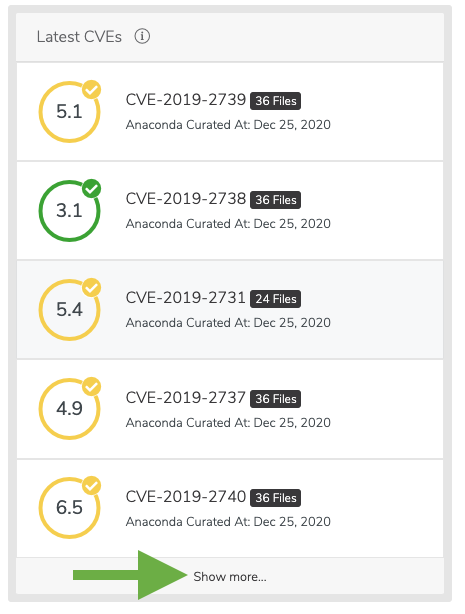
Viewing the details of CVEs
Via the UI You can view a list of the latest CVEs at the top of the dashboard. Additionally, you can click Show more at the bottom of the list to view a larger list of CVEs. From there, click an individual CVE to view further details.