Before you begin
Anaconda highly recommends you have knowledge of your LDAP server and organizational structure to complete this procedure. Configuring identity and access management is complex, and each enterprise has a unique LDAP directory structure. While your implementation will be based on the specific structure and needs of your organization, the principals and processes described here will enable you to:- Gather directory information about your LDAP server.
- Establish a connection to your LDAP server in Keycloak.
- Reduce the number of users that need to be mapped into Anaconda through the use of groups and roles.
- Reduce the number of groups that need to be mapped into Anaconda by filtering groups.
- Automate importing new groups for team memberships based on filters.
- Automate the provisioning of permissions to users based on group membership.
Prerequisites
You must have credentials for the “bind user” service account to perform this task. If you do not have the proper credentials, get them from your LDAP Server Administrator.Gathering directory structure information
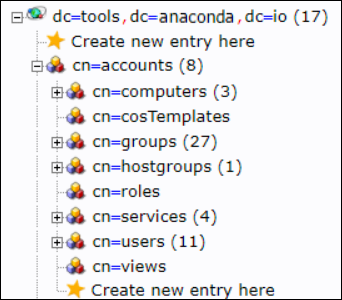
In order to configure Keycloak to validate credentials from your external LDAP server, you need to gather some information about your LDAP directory structure. You’ll use this information to link user attributes (object classes, email, user ID, password, and so on) for use in Anaconda. While you cannot discern a complete picture of your LDAP directory structure from the bind user credentials, you can make some general assumptions about it based on them. For example, if the bind user distinguished name (DN) is:uid=binduser,cn=users,cn=accounts,dc=tools,dc=anaconda,dc=io
We can see the “root” or “base” of the directory tree is dc=tools,dc=anaconda,dc=io. From there we can discern the rest of the tree structure. In this example, we can see that the uid attribute is stored in the users folder, which is stored in the accounts folder.
If you prefer, tools are available to aid in the visualization, navigation, and updating of your organization’s LDAP directory server, such as phpldapadmin, which was used to generate the following view. This provides additional information about the LDAP structure that you can’t discern from just looking at the bind credentials, such as the location of groups, which is also stored in the accounts folder.
ldapsearch tool, along with the bind user credentials, to learn details about an individual user based on their User ID. For more information about the ldapsearch tool, see the official documentation.
Gather the information you’ll need to configure user federation within Keycloak by running the following command against a known user ID:
User1 the command would look like this:
Setting up LDAP user federation
Now that you have gathered information about your directory, you need to tell Keycloak how to interpret that information, so it can use it with Anaconda software.These attributes can be remapped later, if necessary.
- Log in to your Keycloak console using an account that has administrator privileges.
- Select User federation from the left-hand navigation menu.
- Select ldap from the Add provider… dropdown menu.
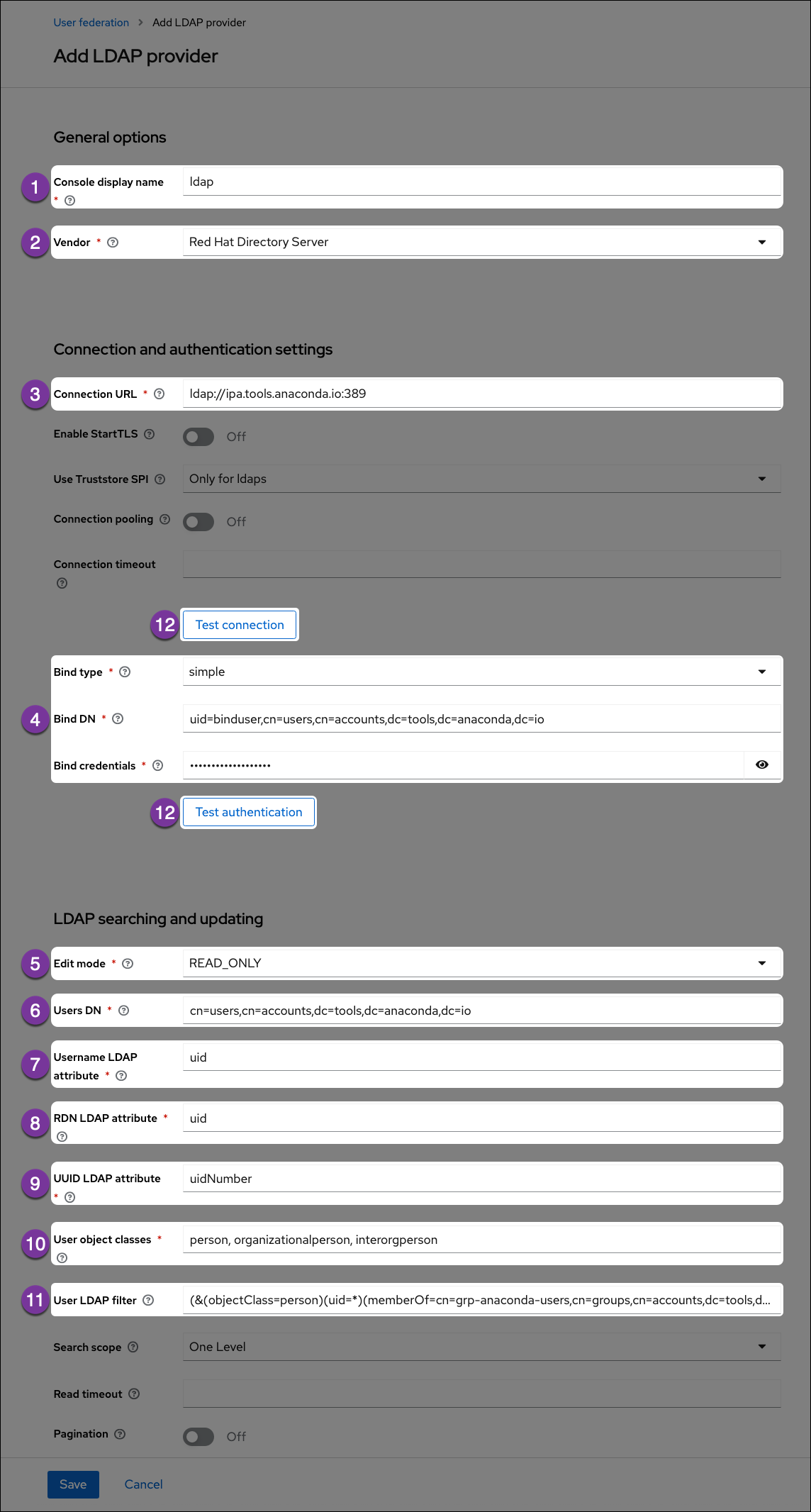
- Console Display Name: Enter a name for Keycloak to display for the LDAP server.
- Vendor: Select your LDAP server vendor from the dropdown menu. If you do not know your vendor, ask your LDAP server administrator.
- Connection URL: Enter the LDAP server’s URL here.
- Bind User information: Enter the bind user information here.
-
Edit Mode:Set the edit mode to
READ_ONLYso you can view and import user information but don’t have to worry about making unwanted changes to your LDAP server. - Users DN:Enter the LDAP directory location for your users here.
-
Username LDAP attribute: Get this information from your
ldapsearchreturn. This attribute determines what is displayed as your user’s name when they sign into Anaconda. In this example, the username attribute isuid. -
RDN LDAP attribute: Get this information from your
ldapsearchreturn. Usually, the relative distinguished name (RDN) attribute is the same as the username attribute, but this field may default to something else depending on your vendor. -
UUID LDAP attribute: Get this information from your
ldapsearchreturn. Your users’ unique identifiers (UUID). -
User object classes: Get this information from your
ldapsearchreturn. Generally, the user object classes field will have more than one entry, separated by a comma. -
User LDAP filter: The user LDAP filter restricts which users are returned from your LDAP directory. In the example, we only want users with the attribute
objectClass=personthat also have auidand are in the groupcn=grp-anaconda-users. Because users must explicitly be added to the group, unauthorized access is prevented, and license management is simplified. Filters also limit the need to synchronize a large number of objects from LDAP, which will help prevent out-of-memory errors in the auth pod. - Test buttons: Use the Test connection and Test authentication buttons to verify that Anaconda can connect to the provider with the credentials provided. You’ll need to resolve any errors before continuing.
Configuring Group Mappers
Once user federation is established, you can set up a group mapper for Keycloak to import your LDAP server’s groups automatically for you. Once again, use theldapsearch tool to gather information about your LDAP directory, only this time, look for information pertaining to your organizations groups.
To gather information about groups in your LDAP directory, run the following command against a known group DN:
- Select User Federation from the left-hand navigation.
- Select your LDAP server.
- Select the Mappers tab.
- Select Add mapper.
- Enter a name for your group mapper, such as ldap_group_mapper.
- Select group-ldap-mapper from the Mapper Type dropdown menu. More options will appear based on your dropdown selection.
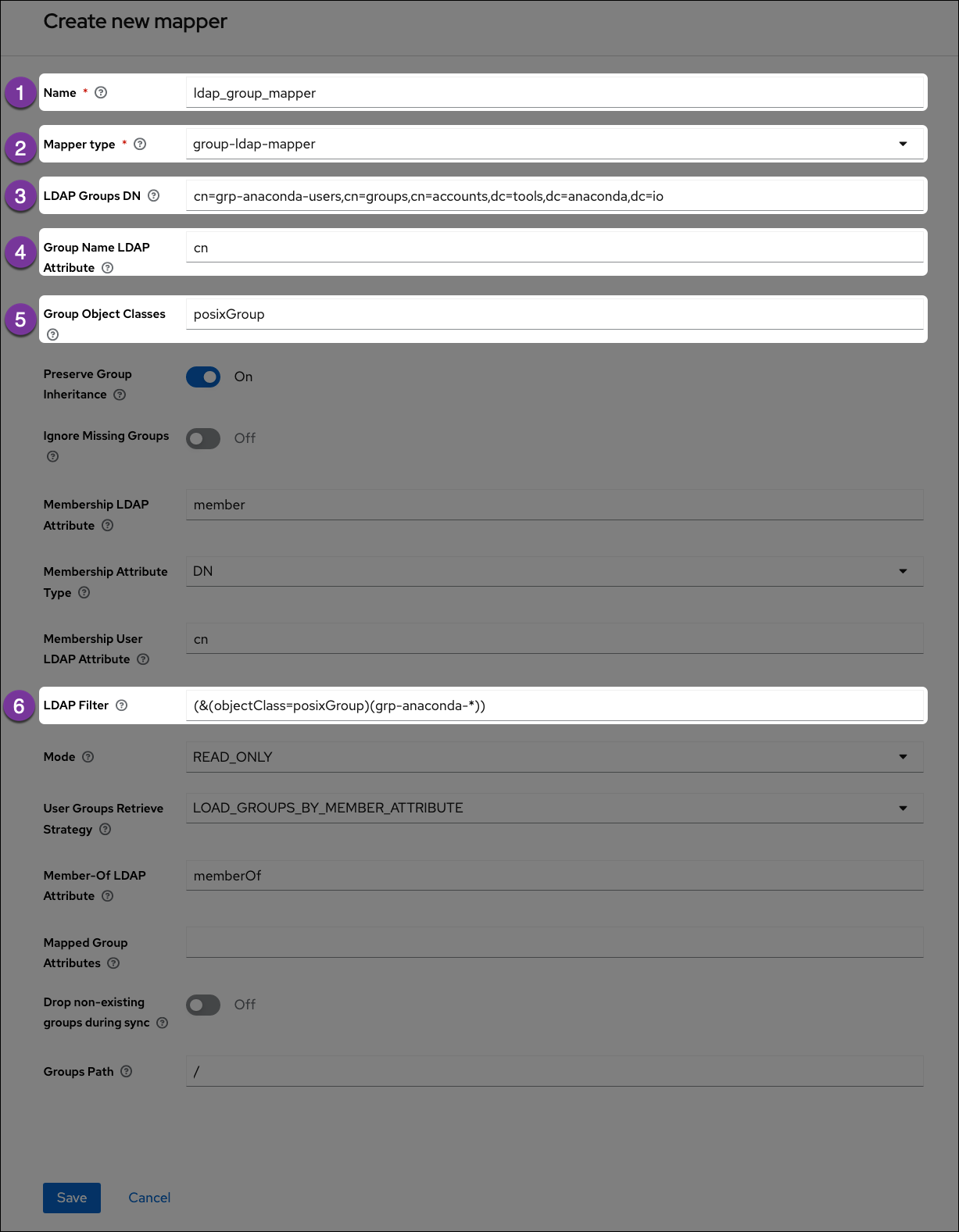
- Name: Enter a name for Keycloak to display for the LDAP group mapper.
- Mapper Type: Select group-ldap-mapper from the dropdown menu.
-
LDAP Groups DN: Get this information from your
ldapsearchreturn. Provide the distinguished name of the group you would like to map. -
Group Name LDAP Attribute: Get this information from your
ldapsearchreturn. Enter the attribute that is associated with groups. In this example, the attribute iscn. -
Group Object Classes: Get this information from your
ldapsearchreturn. This field will often have multiple entries, separated by a comma. -
LDAP Filter: If you have established groups of users in your LDAP server that you plan to provide with access to Anaconda, you can import those specific groups by providing search filter criteria here. However, depending on how your LDAP server is structured, filtering to the correct groups can be complicated.
The search filter utilizes regular expressions (that is, it supports the use of wildcard characters). This example shows the search filter as
grp-anaconda-*, which will reach out to the LDAP server and import all groups that begin withgrp-anaconda-.
Mapping group roles
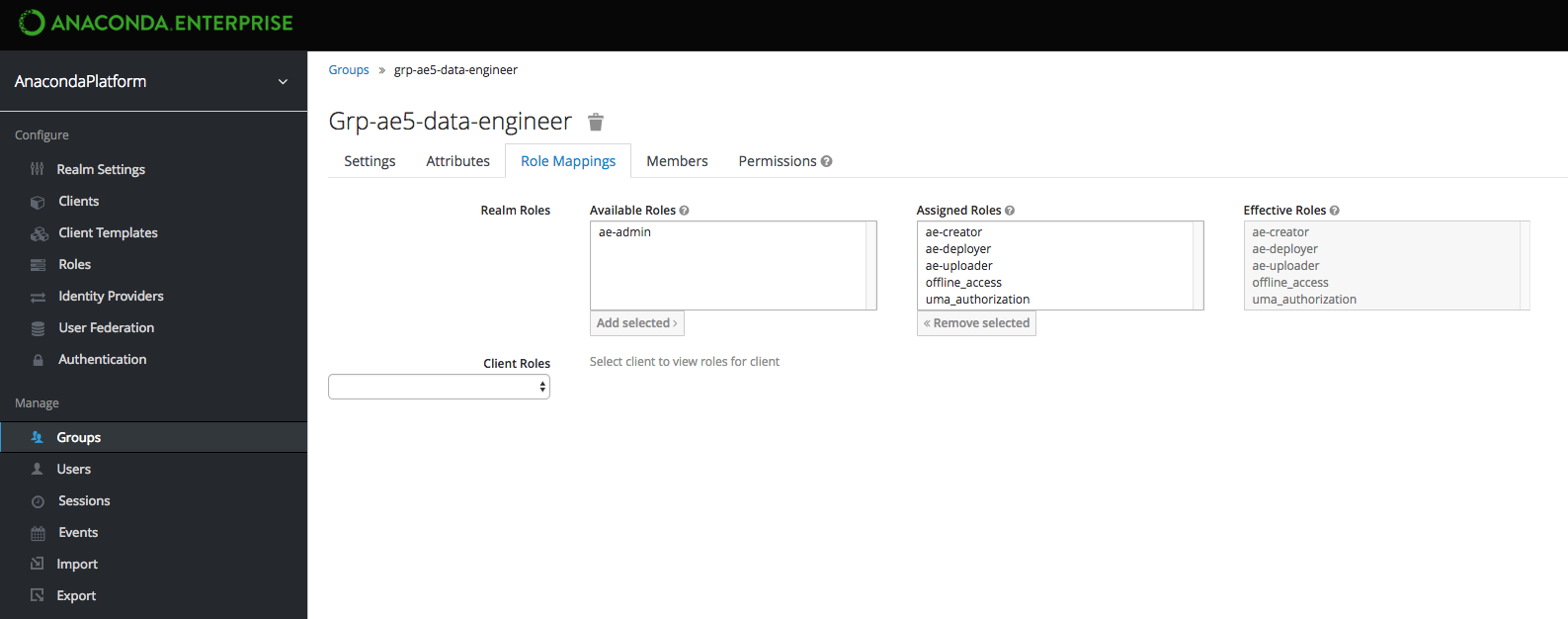
If you have groups of users that you plan to provide with access to Anaconda, you can import them using the LDAP filter as described above. Once complete, you need to provide your groups of users with permissions to work within Anaconda. Roles determine a user’s permissions within Anaconda, and a set of “realm” roles are established for you by default when you install. As a final step in establishing a connection to your LDAP server, you can map these provided roles to groups within your LDAP server to provide your team members with everything they need to work within Anaconda. Once the group roles are established, if a new team member arrives, adding them to the correct LDAP group provides them with all the correct permissions they need to use Anaconda right away. For more information about roles, see Roles and groups. In the example below, groups have been established within the LDAP Server specifically for Anaconda users. Roles have been assigned to these groups to provide their members with the “proper” level of functionality within Anaconda for them to perform their jobs. A brief explanation on what their set role permissions will allow them to do has been provided in the right-hand column.| LDAP Group | ae-admin | ae-creator | ae-deployer | ae-uploader | offline_access | uma_authorization | Description |
|---|---|---|---|---|---|---|---|
| grp-anaconda-biz-analyst | X | Business Analysts can access the system. They cannot create projects or grant others access to the system. | |||||
| grp-anaconda-data-scientist | X | X | X | X | X | Data Scientists can create and share projects, but cannot deploy them. | |
| grp-anaconda-data-engineer | X | X | X | X | Data Engineers can additionally deploy projects, as well as grant access to others. | ||
| grp-anaconda-devops | X | X | X | DevOps can deploy projects and upload packages, but cannot create projects. | |||
| grp-anaconda-sec-admin | This group should be used to administer user access within the system. Therefore, no roles should be defined in the AnacondaPlatform realm. If required, roles can be defined and access granted in the Auth Center Master realm. | ||||||
| grp-anaconda-sysadmin | X | By default, the ae-admin role is a superuser for all other roles. | |||||
| grp-anaconda-sysacct | The roles for system accounts are yet to be defined. These could be used for automated CI/CD tasks. | ||||||
| grp-anaconda-users | This is used as a coarse-grained control for access to AE5, so no roles are defined. |
Configuring LDAPS
LDAP over SSL, or LDAPS, allows you to encrypt your LDAP server data while it travels during communications, in order to protect it from attacks like certificate theft. For more information, see the official Keycloak documentation on LDAPS.Prerequisites
You must have the Javajre package installed to complete this procedure.
You must have SSL/TLS certificates for your LDAP server.
Establishing LDAPS
- Gravity
- BYOK8s
If you are using a custom certificate authority (CA), you must create a truststore on your host. If you are using a public CA, you can skip the truststore installation and go straight to exporting your existing SSL certificates to the Anaconda Enterprise auth service.Here is an example of what your 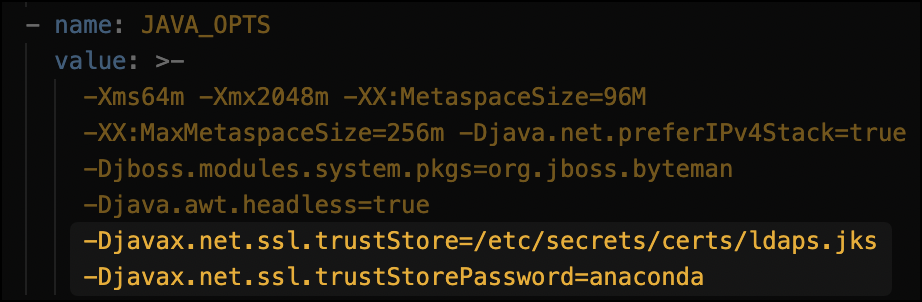
-
If the CA certificates are directly available to you, generate your truststore by running the following command:
If you need to add an intermediate certificate, run this command again with a unique alias, to include it in the
LDAPS.jksfile. -
Export the existing SSL certificates for your system by running the following commands:
-
As a precautionary measure, create a backup of the
secrets-exported.ymlfile prior to encoding it by running the following command: -
Run the following command to encode the newly created truststore as
base64: -
Copy the output of this command, and paste it into the
datasection of thesecrets-exported.ymlfile. -
Run the following command to update Anaconda Enterprise with the secrets certificate:
-
Verify that the
LDAPS.jksentry has been added to the secret: -
Run the following command to restart the
authservice: -
Create a backup of your current auth configuration:
- Edit the auth pod deployment:
- Add the below to the
JAVA_OPTSkey/value:
auth.yaml file’s JAVA_OPTS might look like when complete.
- Save your changes.