For all new users
- Log in to the Keycloak administrative console.
- Navigate to the dev realm.
- Select Realm settings from the left-hand navigation.
-
Select the Themes tab.
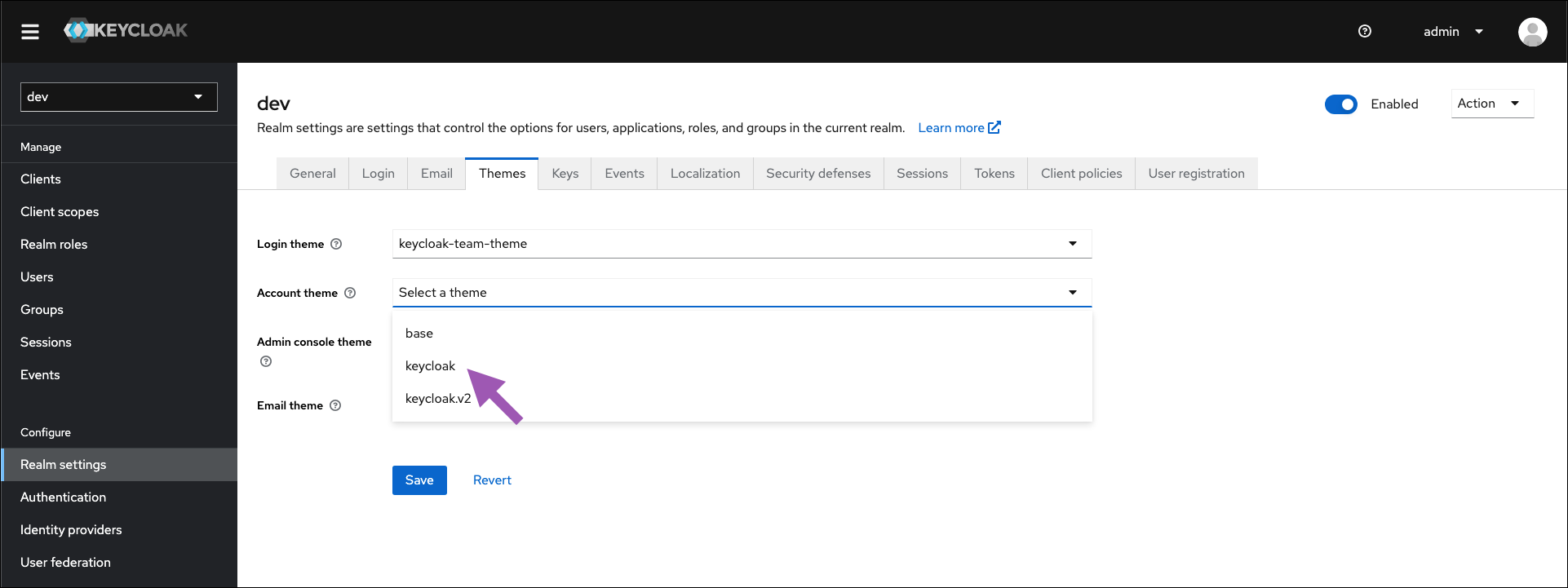
- Open the Account theme dropdown menu and select keycloak from the list.
- Click Save.
- Select Authentication from the left-hand navigation.
- Select the Required actions tab.
-
Find Configure OTP in the Required actions column, and toggle Set as default action to
ON.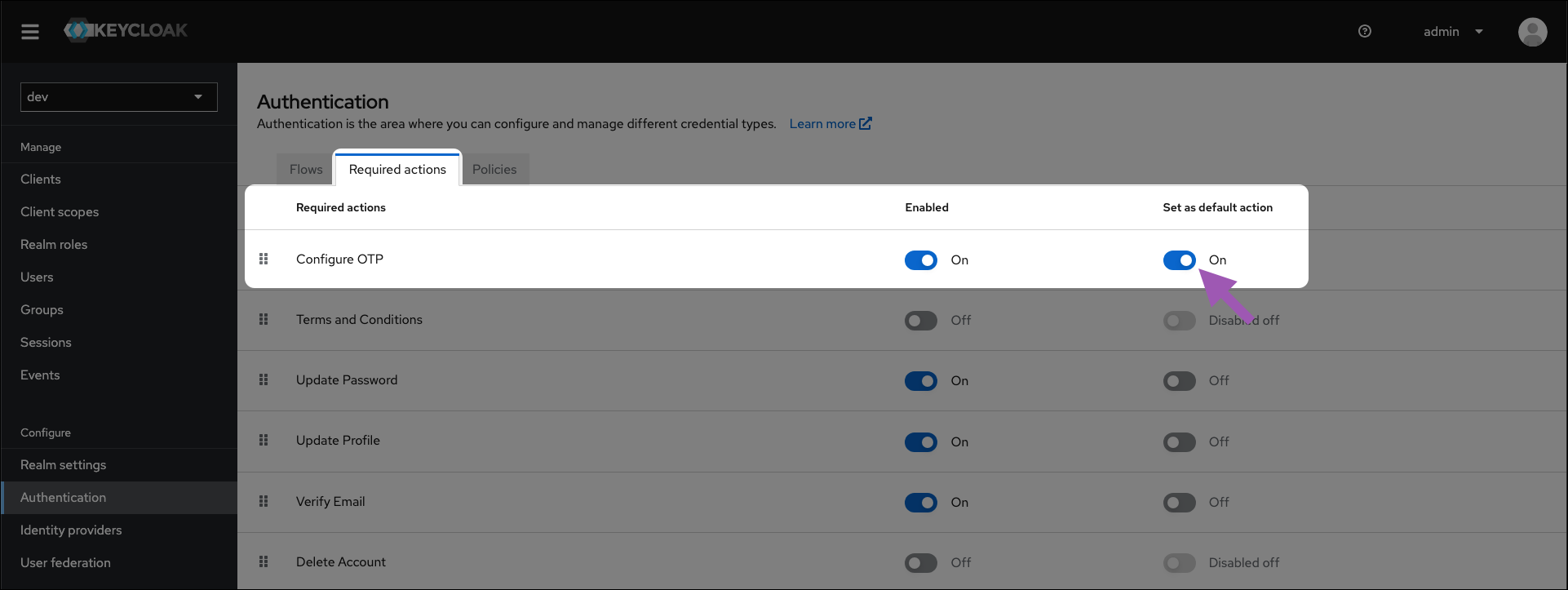
For existing users
This must be done for every user that does not have an OTP configured.
- Log in to the Keycloak administrative console.
- Navigate to the dev realm.
- Select Users from the left-hand navigation.
- Select a user from the list to view their profile page.
- Open the Required user actions dropdown menu and select Configure OTP.
- Click Save.