For new users
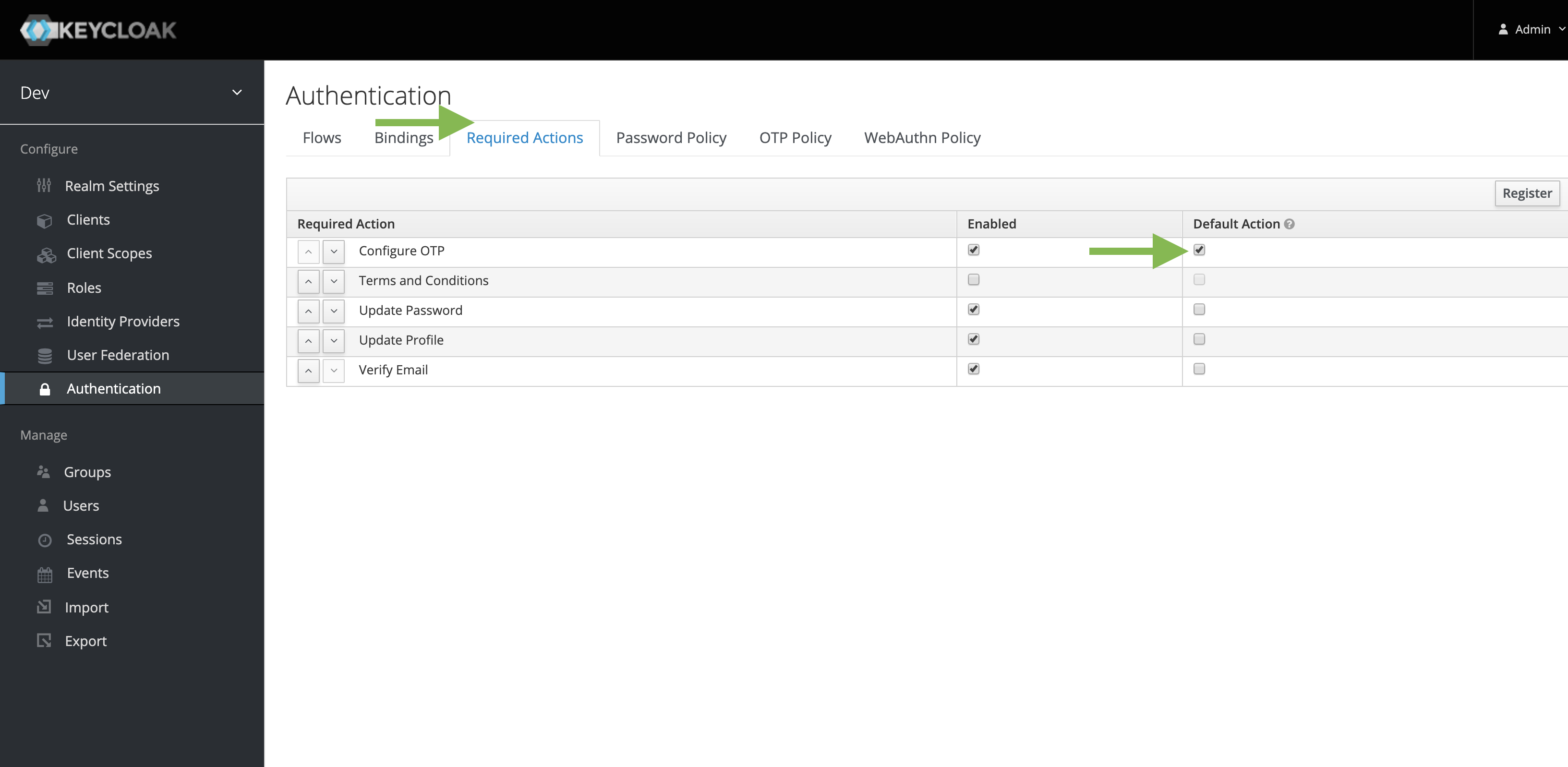
- Go to Authentication.
- Navigate to the Required Actions tab.
- Under Configure OTP, select Default.
For existing users
This should be done for every user that does not have an OTP configured.
- Go to the user profile page.
- Under Required Field, select Configure OTP.